What’s the problem exactly?
With the rise of the availability of web based applications, web based versions of their client-server counterparts, and workforce mobility, comes the increased risk of potentially leaving behind sensitive information on remote devices not under the control of corporate IT. While there are no 100% solutions to this problem, organizations can implement numerous preventative measures to deal with it which are available from the developer as well as 3rd party technologies.
Microsoft Outlook Web Access is no exception to this problem and is often at the forefront of the concerns of security teams because of it’s popularity and the fact it is very often exposed to the public internet so that mobile work forces can remain productive from anywhere. This is of course exacerbated by the fact that OWA and other web based email interfaces like it provide access to email attachments. These attachments, when opened, are cached in a browser’s Temporary Internet Files folder or worse perhaps saved to a folder location that is easily accessible by anyone. End-users could potentially walk-away from these devices leaving corporate information behind to possibly be exploited for malicious purposes.
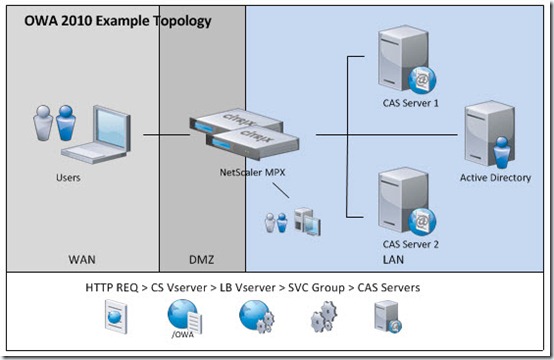
As mentioned, there is no solution that is 100% safe to the aforementioned problem. There are numerous solutions to these issues, ranging from VPN Cleanup Agents, to access via Virtualization technologies such as Citrix XenApp or Citrix XenDesktop, to proxy devices such as Citrix NetScaler. Each method has their own set of pros and cons and have varying levels of cost and preventative . This article focuses on utilizing the power of Citrix NetScaler ADC
How can one solve this problem?
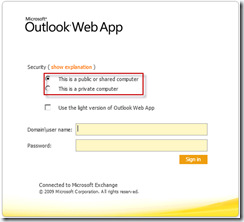
Starting with Exchange Server 2007, Microsoft introduced the concept of Public and Private computers allowing end-users to select whether their end device was to be trusted or not.
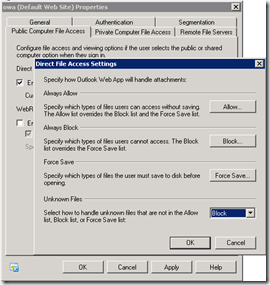
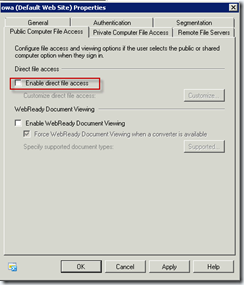
On the Exchange Server end, these options pertain to settings that can be used to control the behaviour of how attachments are dealt with. These include the ability to block all attachment access or allow attachment access but only via the built-in document conversion utilities which convert the attachment to HTML for view right in the browser.
 |
|
|
Disallow all attachment access or only allow file preview |
Allow attachments with restrictions or certain file types only or force use of file preview |
These settings in turn control the end-user experience with regards to attachment access.
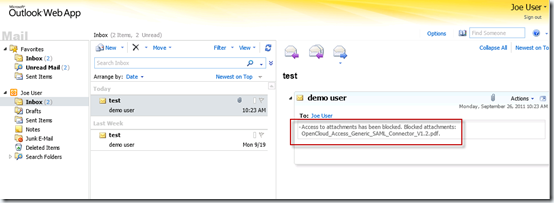 |
| Public computer with no access to attachment |
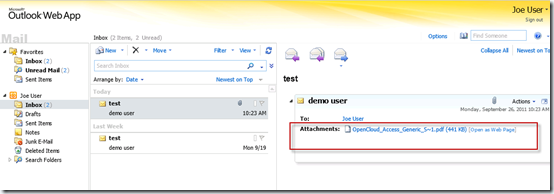 |
| Private computer with attachment access and preview |
Giving end-users the control is not the answer
All of the above are great options if you actually trust your end users to select the correct option at login to classify the type of device or location they are accessing your network from. But a more realistic solution is to profile the device, user, or location and enforce the behaviours based on this discovery information. Some examples of the information you could base a decision on include:
- Client IP Source Address
- SSL Certificate Auth/Details
- Browser/Device Type
- User Identity or Group Membership
- Presence of Anti-Virus or Anti-Spam software
How can Citrix NetScaler ADC help?
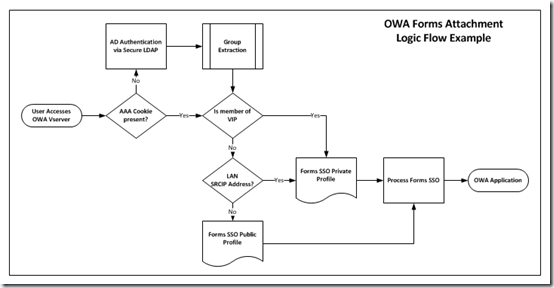
NetScaler has three core features which can be leveraged to secure Outlook Web Access attachment functionality based on the methods described above. The NetScaler AAATM feature (Authentication, Authorization, and Accounting for Traffic Management) enables the ability to use the NetScaler to perform authentication to user account directories based on LDAP, RADIUS, TACACS+, or Client SSL certificates. Secondly, Access Gateway functionality provides bi-directional SSL VPN tunnelling and ICA Proxy capabilities and adds the ability to perform endpoint analysis to the aforementioned AAA features provided by AAATM. And lastly, the NetScaler Rewriting feature allows us to alter or inject html in Requests and Responses based on conditions we define by the very extensible AppExpert policy engine.
Instead of letting the End User control the attachment behavior, the NetScaler can be inserted in front of the solution to provide
- DMZ Authentication and Authorization
- Single Sign-On to Outlook Web Access
- Attachment control based on end user, location, or device attributes
In the configuration example below, Source Address and Group Membership are chosen for example to determine the level of attachment security applied to the session.
In addition to providing attachment security, Citrix NetScaler can be leveraged to provide High Availability, High Scalability, and Consolidation through additional on-box features such as SSL Offload, Content Switching, Load Balancing, Content Compression, and Integrated Cache.
Sample NetScaler AAATM Configuration for OWA 2010 Sample Access Gateway Configuration (coming soon)
More Information
- Citrix NetScaler Deployment Guide for Microsoft Exchange 2010
- Citrix NetScaler AppExpert Template for Outlook Web Access
- How to Configure Single Sign-On for Outlook Web Access 2010
- How to Configure Single Sign-On for Outlook Web Access 2007



 Posted by Bellihammer
Posted by Bellihammer